These days, simply having a password isn’t enough to keep your systems secure from digital threats. Multi-factor authentication (MFA), a system of logging in using two or more credential methods, is no longer the future of login security – it’s become a basic necessity for businesses. With cybersecurity threats becoming increasingly sophisticated, MFA is one of the best ways to prevent unauthorized parties from accessing important systems or data at your agency. We’ll take a look at what MFA is, what its benefits are, and how to go about implementing MFA at your agency.
In this article:
- Why use MFA?
- Types of MFA
- Implementing MFA at your agency
- Does HawkSoft use MFA?
Why use MFA?
Here are just a few of the reasons why using MFA should be a no-brainer for every insurance agency – and organizations of any size in general.
It reduces cybersecurity risks
There are more cybersecurity risks to organizations today than ever before, with malware attacks at an all-time high and the surge in cloud and remote work environments creating additional vulnerabilities for all businesses.
 While MFA isn’t the only step your agency should take to protect the security of your systems and data, it’s certainly an effective one. Simply implementing MFA makes it nearly impossible for attackers to infiltrate your systems with a stolen password alone, which is one of the most common and frequent types of attack. Threat actors target organizations with weak security that require less effort to gain access to, so implementing MFA is one of the easiest, most effective ways to block the majority of attacks.
While MFA isn’t the only step your agency should take to protect the security of your systems and data, it’s certainly an effective one. Simply implementing MFA makes it nearly impossible for attackers to infiltrate your systems with a stolen password alone, which is one of the most common and frequent types of attack. Threat actors target organizations with weak security that require less effort to gain access to, so implementing MFA is one of the easiest, most effective ways to block the majority of attacks.
“MFA is one of the most basic cybersecurity controls, but it can be enough of a hurdle to put a threat actor off,” John Menefee (Cyber Product Manager at Travelers) recently told Insurance Business. “A lot of the claims that we see are email compromise events – when a threat actor gains access to an employee’s username and password and uses that to access their web-based email account. Something as simple as requiring MFA to gain access to that email account, even if it’s just a text message to a cell phone (which is probably one of the least secure versions of MFA) is probably enough to deter most email compromises that we see.”
“A lot of the claims that we see are email compromise events – when a threat actor gains access to an employee’s username and password and uses that to access their web-based email account. Something as simple as requiring MFA to gain access to that email account…is probably enough to deter most email compromises that we see.”
John Menefee (Travelers) to Insurance Business
It may be required by law or contract
There are a number of data security regulations that affect insurance agents, such as the Gramm-Leach-Bliley Act (GLBA), the New York Department of Financial Services (NYDFS), and other state insurance data security laws (generally based on the National Association of Insurance Commissioners Insurance Data Security Model Law). State privacy laws may also dictate MFA as a requirement in appointment contracts.
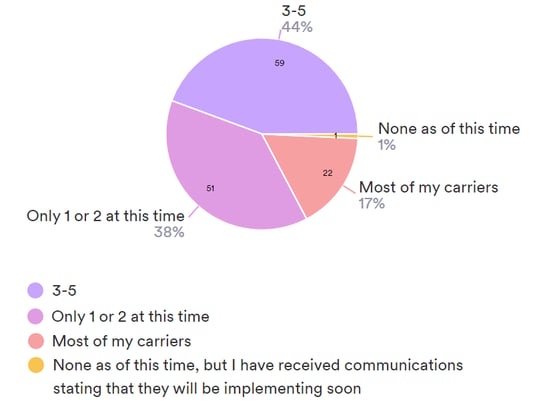
It’s becoming more and more commonplace for carriers to require agents to log in using MFA as well. ACT’s recent study on MFA found that 60% of carriers said they are implementing MFA for agent portals, comparative raters, and more, with most of the remaining portion planning to implement MFA in the future.
ACT survey to independent agents:
How many of your carriers currently require MFA?
MFA is quickly becoming the security standard, and agencies who don’t have MFA as an additional layer of security become the weak link in the data supply chain. With so many parties handling an insured’s data, any weak point can put clients’ personal data at risk. Megan North of Amwins told Insurance Business America on the topic, “The stronger we can make those entities with weaker cybersecurity, the more resilient we are as a whole. So, we are seeing a lot more collaboration across the supply chain from insurance carriers to security vendors, brokers, and insureds. It’s a more holistic effort, and we’re all benefiting from it.”
“The stronger we can make those entities with weaker cybersecurity, the more resilient we are as a whole. So, we are seeing a lot more collaboration across the supply chain from insurance carriers to security vendors, brokers, and insureds. It’s a more holistic effort, and we’re all benefiting from it.”
Megan North (Amwins) to Insurance Business America
It’s a quick and easy way to log into systems
An added benefit of MFA is that it’s often actually a more convenient login method than traditional passwords. No need to remember a host of different passwords for each site. While there are different types of MFA authentication, most are very simple, ranging from entering a verification code sent to your phone or email to simply using facial or fingerprint recognition.
It ensures only authorized users access systems
Many employers prefer MFA to other login methods because it prevents employees from sharing logins with others who should not have the authority to access certain data or systems. It also makes it easy to revoke access when employees leave, without having to reset passwords in multiple systems each time.
Types of MFA
There are many types of MFA applications available, but they all rely on two or more authentication factors. The most common MFA platforms use a combination of several of these factors:
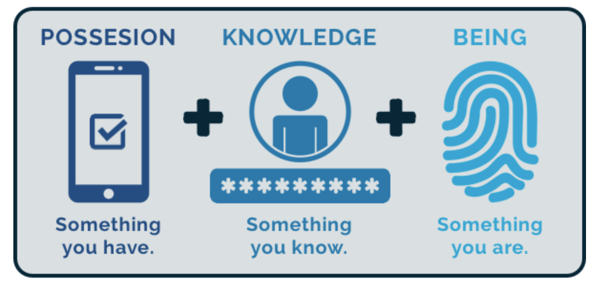
- Possession
This is an item that only you possess, including your phone or email account, software tokens or certificates, or a badge or key fob. - Knowledge
This is something you know, like a password, PIN, or personal security question. - Being (inherence)
These are biometrics (unique physical traits) like fingerprints, facial recognition, or retinal scanning.
For example, an MFA solution could ask for your password (knowledge) and then send a verification code to your phone for the second form of authentication (possession). More sophisticated MFA systems, especially those used for extremely sensitive data or systems, may use additional authentication factors such as:
- Location
You may only be able to log into systems from devices within a certain geographical area and/or from a particular IP address. - Behavior
You may be restricted from logging in when your behavior deviates from your normal usage of a system, such as outside normal hours, from unrecognized devices or networks, etc.
Implementing MFA
How do you go about implementing MFA at your agency? It’s important to understand the common obstacles to implementation, as well as the steps for successful implementation.
Barriers to implementation
There’s a reason why every organization isn’t already using MFA. Here are a few common barriers to successful MFA implementation, and what you can do to help your agency overcome these obstacles.
User/process disruption
One of the biggest fears with MFA is that it’s an additional step for users, adding time to their already busy workday. While it’s true that like any new process, MFA may take some time for staff to get used to, one of the reasons MFA is so prevalent is that it’s a fairly quick and convenient login process. In fact, ACT’s MFA survey found that most agency respondents see minimal to no agency workflow impact from the implementation of MFA, with less than 3% of agencies indicating that it lengthens workflows or causes staff frustration.
Multiple platforms may require separate MFA logins
Another obstacle for agencies is that they often log into many different systems and carrier portals throughout the day, which may each require separate MFA logins. While a single MFA login doesn’t add much time to the workday, multiple logins can begin to be cumbersome, making agencies hesitant to add another MFA login process to their own internal systems. ACT found multiple logins to be an agency pain point, with agencies desiring a single, consistent approach across carriers and platforms.
One solution for this would be for all parties to employ a single sign-on application, such as SignOn Once, an initiative developed by nonprofit industry coalition ID Federation. As PropertyCasualty360 puts it, this type of tool “creates a single entrance into an overarching hallway of cyber doors. Once a user is granted access to the hallway, they can open any authorized door their MFA key has unlocked.” Such solutions have not yet been widely adopted by carriers and technology vendors, but agencies can continue to advocate for simple industry-wide solutions through venues like ACT.
Phones as authentication devices
Many authentication apps send verification codes to users’ phones, requiring them to have and use a smartphone at their workplace. This may present an issue for agencies who don’t allow personal phones to be used at work, or for employees that don’t own a smartphone. Fortunately, 73% of agencies in the ACT survey say they don’t restrict personal phone usage at work, and another 19% say they would allow phones for MFA authentication only. For employees without their own smartphones, authentication can be done through SMS (text) or email on a device like a work computer.
Steps for implementing MFA
In order to start using MFA at your agency, you’ll need to choose an MFA application, ensure complete and consistent use, and maintain and improve your implementation over time.
Choose an authentication application and method
The most important and time-consuming part of the process will likely be choosing the authentication application and method that works best for your agency. There are a host of authentication applications available, including both free and paid options. You’ll need to do some research to determine which app will work best with your agency’s setup, as well as which authentication method to use (text, email, biometric, etc.).
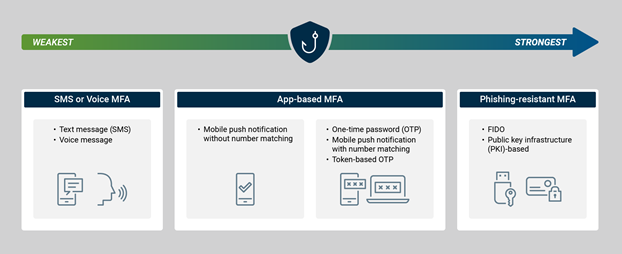
Remember that not all MFA solutions provide the same level of security. The US Cybersecurity & Infrastructure Security Agency (CISA) recommends implementing phishing-resistant MFA solutions for the highest level of security, including solutions like FIDO and public key infrastructure (PKI-based) authentication, which provide an additional level of security that can block logins to fake websites. However, any level of MFA is better than none, so you may want to start with a simple and easy to implement solution and work your way up to a more comprehensive one.
Security strength of MFA by method
Ensure consistent, comprehensive implementation
An online environment is only as secure as its weakest point. For an MFA solution to be successful, it needs to protect your entire environment and all users, without any gaps or exceptions. “Multi-factor is important, but it’s also equally important how it’s implemented,” Preston Miller of Unit 42 at Palo Alto Networks recently told Insurance Journal. “What I often see is that organizations have it turned on, but it’s not fully configured. Or they allow alternative methods of authenticating for accounts that don’t support multi-factor authentication, so you’re giving threat actors another avenue to access your data and bypassing the security control you’re hoping to implement in the first place.”
Work with your IT admin to make sure your MFA solution is fully configured, consistently implemented, and set up to protect any environment that accesses internal systems or data. Don’t make exceptions for any employees, which can become dangerous weak spots in your security.
“Multi-factor is important, but it’s also equally important how it’s implemented. What I often see is that organizations have it turned on, but it’s not fully configured…so you’re bypassing the security control you’re hoping to implement in the first place.”
Preston Miller (Unit 42, Palo Alto Networks) to Insurance Journal
Maintain and increase security over time
No security solution should be “set it and forget it.” Monitor your solution to make sure it’s effective, minimize issues for users, and optimize it as needed. Cybersecurity threats are constantly evolving, so your security solution should too. Make sure you keep the application updated to make use of security updates and patches. Once you have a stable MFA solution in place, you can determine what the next level of security looks like for your agency and how you can get there.
Does HawkSoft employ MFA?
HawkSoft employs MFA internally within our own organization to ensure the highest level of security for internal systems and data, and recommends that all agencies do the same. We also provide options for customers to enable MFA when logging into HawkSoft.
HawkSoft Online customers
For new HawkSoft Online customers, MFA is now enabled by default when logging into the online environment. Existing HawkSoft Online customers can enable MFA at any time as well, with the permission of the agency’s admin. This is available at no additional cost.
Agencies can choose the MFA application they’d like to use from popular apps like Microsoft Authenticator, Google Authenticator, Authy, and LastPass. HawkSoft Online then uses the chosen platform to send a one-time password (OTP) to your phone or device with the authenticator application installed. This password is entered before signing into HawkSoft as normal. Search “MFA” in the Help Portal in HawkSoft for detailed instructions on setting up MFA.
Local installations
Agencies with local installations of HawkSoft are responsible for enabling MFA on their own if desired. This can be done at no additional cost using free authenticator applications.
HawkSoft 6 & beyond
In HawkSoft 6 and later versions, MFA will be enabled by default for all agencies as a necessary layer of security for accessing data in the cloud. Recognized devices that have recently logged in using MFA will be allowed to log into HawkSoft, while unrecognized devices will send a verification code to the user’s email account.
Make security a priority with MFA
Implementing MFA at your agency is an important piece of the data security puzzle for agencies. With no-cost solutions available, every agency can afford to take this crucial step in protecting their systems and the sensitive data they house.














































