Boost Your Microsoft 365 Security

Boost Your Microsoft 365 Security
October 20, 2025
3
min read
Building a Cybersecurity Culture in Your Agency


Building a Cybersecurity Culture in Your Agency
October 12, 2025
3
min read
Defining IT and Cybersecurity: Core Functions and Objectives


Defining IT and Cybersecurity: Core Functions and Objectives
October 3, 2025
2
min read
IT vs. Cybersecurity - Do you have a gap in services?
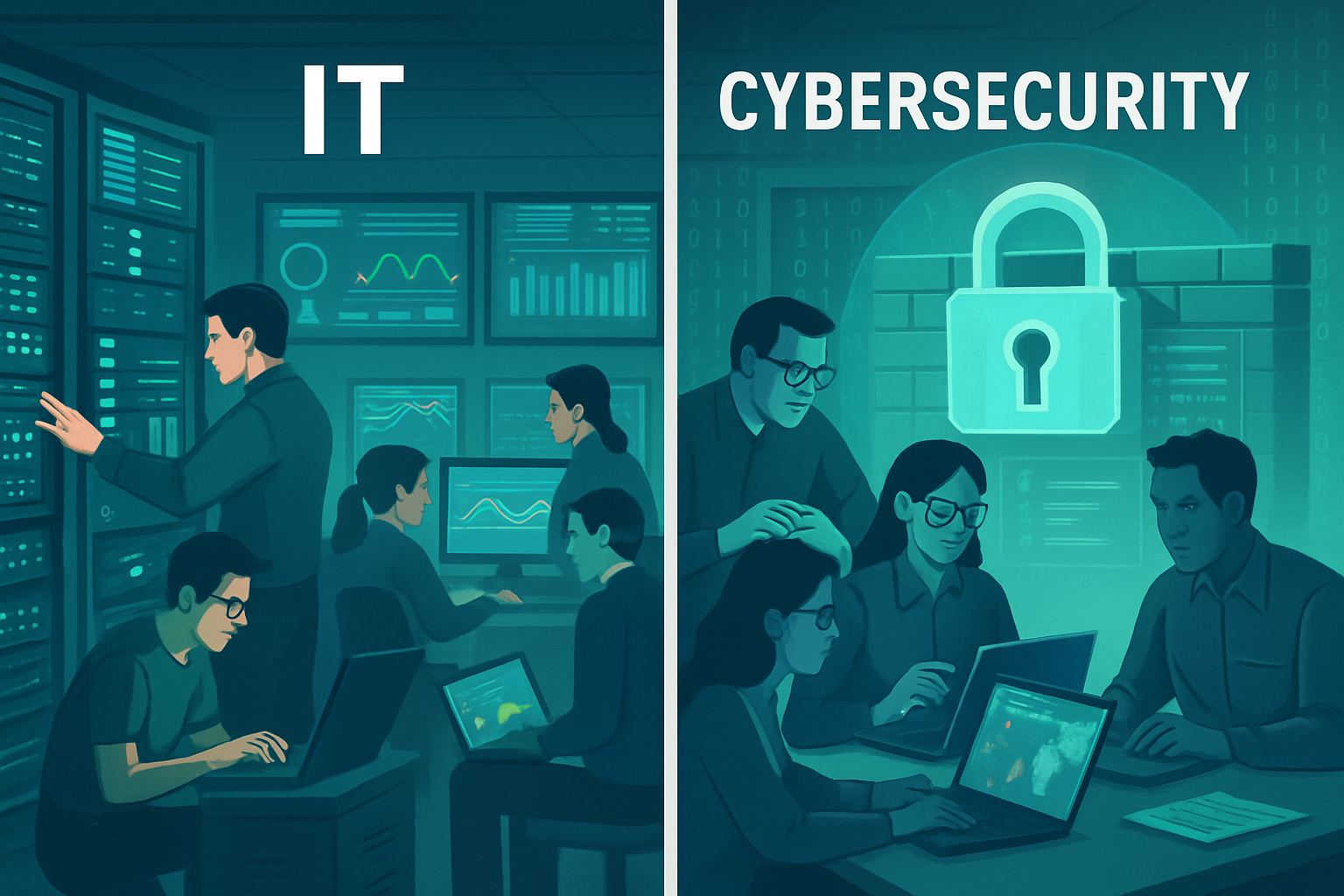

IT vs. Cybersecurity - Do you have a gap in services?
September 24, 2025
6
min read
Safeguard Your Organization Against Phishing Attacks


Safeguard Your Organization Against Phishing Attacks
September 22, 2025
2
min read
Navigate the Complexities of Data Security and Compliance


Navigate the Complexities of Data Security and Compliance
September 14, 2025
2
min read
Catalyit August TechTips Roundup: Insights, Trends & Tools


Catalyit August TechTips Roundup: Insights, Trends & Tools
September 1, 2025
1
min read
July TechTips Roundup: Practical Insights, Emerging Risks, and Smarter Tech Moves


July TechTips Roundup: Practical Insights, Emerging Risks, and Smarter Tech Moves
July 31, 2025
1
min read
Is Your Agency Exposed? July’s SharePoint Vulnerability Explained


Is Your Agency Exposed? July’s SharePoint Vulnerability Explained
July 23, 2025
4
min read
Why Should I Retake the Agency Tech Assessment?

Why Should I Retake the Agency Tech Assessment?
July 15, 2025
1
min read
The Importance of a Solid AI Cybersecurity Policy


The Importance of a Solid AI Cybersecurity Policy
July 11, 2025
3
min read
How Independent Insurance Agencies Are Using AI to Boost Productivity and Manage Risk

How Independent Insurance Agencies Are Using AI to Boost Productivity and Manage Risk
June 26, 2025
2
min read






















































